With the Society for Terrorism Research (STR) 8th Annual International Conference fast approaching, STR, partnered with the Center for Terrorism and Security Studies (CTSS), is launching a series of guest blog posts, written by those who will be presenting their research at STR14. In the seventh installment of this series Jeff Weyers and Professor Jon Cole discuss their work applying the structured professional judgment tool known as the Identifying Vulnerable Persons (IVP) to extremist activity on social media. Jeff Weyers and Prof. Jon Cole are working on this project as members of the University of Liverpool Tactical Decision Making Research Group.
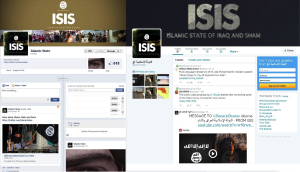
Infamously in Al-Qaeda’s first online issue of Inspire magazine, one of the articles included was a piece called, “Build a Bomb in the Kitchen of Your Mom”. The release by Al-Qaeda was significant for several reasons, it was the first time a terrorist group had created a professionally produced e-magazine. It also demonstrated a realization by Al-Qaeda that social media would be key to its ability to recruit, fund raise and spread propaganda in the future. In fact around that same time (in 2009 and 2010) many terrorist groups including Al-Shabab, Hezbollah, Hamas, Babbar Khalsa, and the International Sikh Youth Federation were all transitioning to social media platforms. The reason for this transition was in part due to increasing stresses on traditional forms of hosting information on websites. Terrorist websites are frequently torn down by government agencies and targeted for Denial of Service (DNS) attacks by governments and hackers. This often would require terrorist organizations to change service providers and re-create their websites on foreign servers, thus requiring money, time and technical resources. Alternatively social media platforms by their design are more resilient to such attacks. Their servers are better protected, their services are free and anyone can setup a site in minutes. These services are also incredibly efficient at the “social” aspect of social media. If we look at recent examples like the Islamic State of Iraq and Sham (ISIS) on Facebook and Twitter, we see that they have been able to develop thousand of followers for their sites within hours of going operational (See Figure 1). When their sites were torn down by Facebook they were re-spawned almost instantly, in one documented case “We are all ISIS” was brought back to life 79 times.
Figure 1: Islamic State Page on Facebook and Twitter
In the modern counter-terrorism context, the key question for law enforcement and intelligence agencies is reducing the signal to noise ratio in the online world. As part of the solution, in 2009 we were asked to come up with a structured professional judgment tool to assist in the early identification of persons at risk of engaging in violent extremism as part of the United Kingdom’s PREVENT strategy. After examining a sample of UK and European violent extremists, 16 criteria were identified that could be used to assist in identifying persons at various stages on the path to violent extremism. This structured professional judgment tool is known as the Identifying Vulnerable Persons (IVP) guidance. Since then we have applied the IVP tool against a sample of over 600 post hoc cases representing virtually every known terrorist group. As the IVP is ideologically neutral it works as well with the IRA as it does with ISIS or even ELF
Why will you want to see what we’ve done?
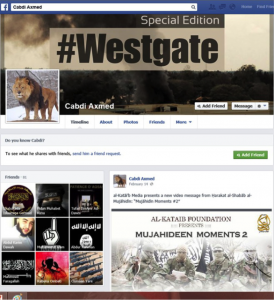
Going back to our discussion about social media, with all of the terrorist groups creating sites on social media it was the perfect opportunity to test the IVP tool against de novo cases online. Here you had virtually every terror group with a platform on social media and thousands of individuals at varying stages of extremism. So taking theses samples we attempted to determine to what extent we could identify persons at risk and were surprised to find that there were in fact hundreds of individuals displaying activities that would be of concern to law enforcement and intelligence agencies. Sometimes this simply meant they were engaged with known recruiters of terrorists groups, sometimes actual threats were made, in other instances individuals were seen with weapons while on these sites (see figure 2).
Figure 2: An example of an extremist profile online
The secondary by-product of this research has included numerous criminal investigations, seizures of weapons, identification of terror cells, deportations of terrorist leaders, identification of terrorist charities and the removal of countless terrorist social media pages. So whilst identification of those ‘at risk’ of engaging in violent extremism is fraught with problems there is clear evidence that there are ways of overcoming those problems. We hope that the STR Conference will allow for practitioners and academics to be able to “show what they got” in terms of new methods for capturing, analyzing and working with data, the goal being that we both can learn from each other and find unique ways for resolving uncommon problems.
Jeff Weyers and Prof. Jon Cole are presenting on “Applying the Identifying Vulnerable People (IVP) guidance: Social media and web 2.0” on Day 2 of the Society for Terrorism Research Conference on Communication and Collaboration for Counter-Terrorism, September 17-19th, in Boston, MA.
A list of all the talks we have at the STR conference is now available via our preliminary program
If you are also presenting at STR14 and would like the opportunity to write a blog post for this series please contact strconference@uml.edu